FAQs¶
General AccuKnox & CNAPP¶
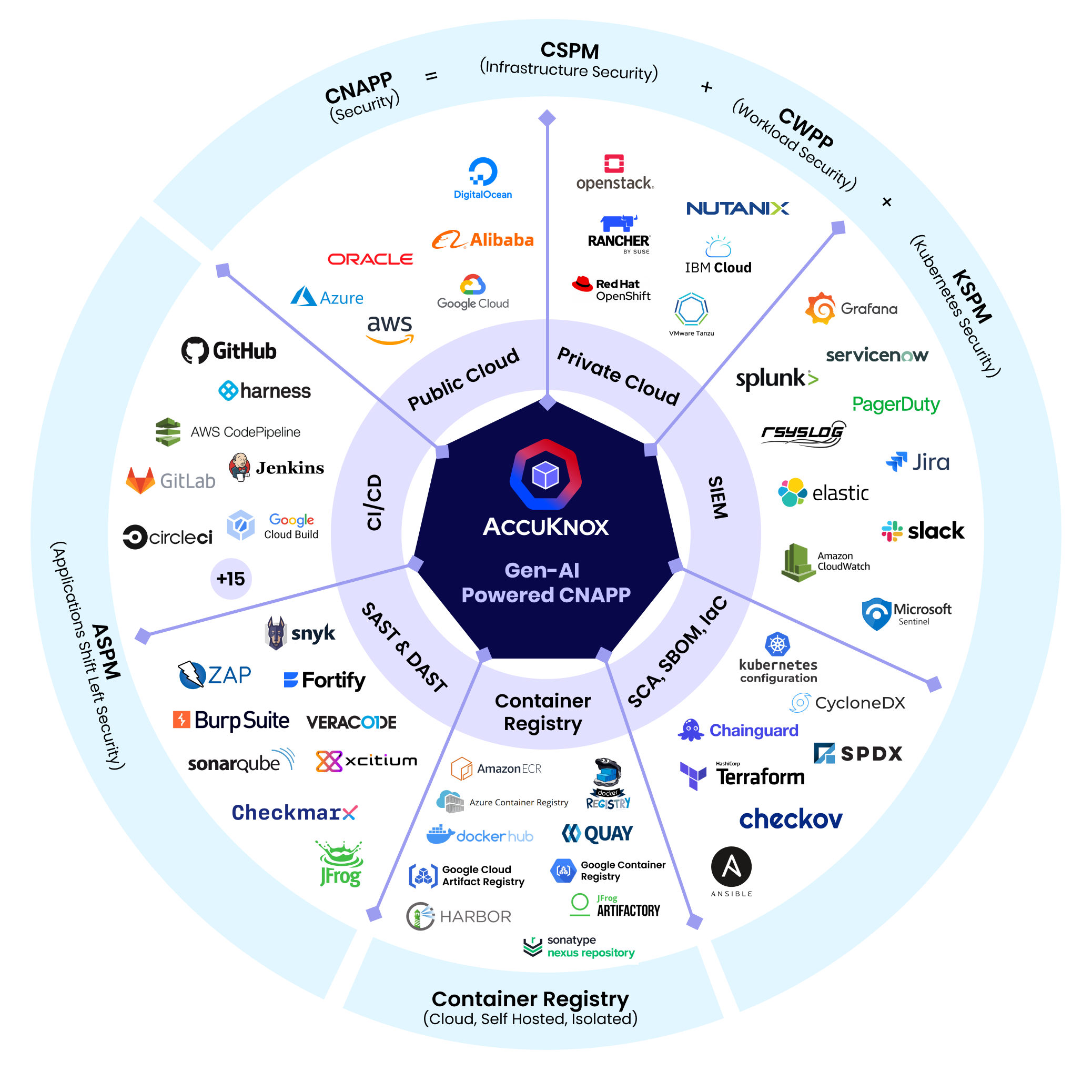
1. What are the modules supported by AccuKnox CNAPP currently?
- CSPM
- ASPM
- DevSecOps security in CI/CD pipeline
- CWPP
- Container Images Scanning
- CDR (Cloud Detection or Response) or CDM (Continuous Diagnostic & Mitigation)
- AI Datasets, Pipelines, Models and Applications
- KSPM
- 33+ Compliance Frameworks
2. What are the platforms and environments that AccuKnox supports?
AccuKnox supports the following environments: + SaaS + PaaS + IaaS
AccuKnox supports the following cloud platforms: + AWS + GCP + Azure + Oracle + OpenStack + OpenShift + Nutanix + VMWare + IBM Cloud
AccuKnox support for the different platforms are as follows: + Kubernetes - Fully supported + Linux - Supported distributions + VMs, Baremetals + 5G Workloads and IoT/Edge Sensors + AI Datasets and LLM Models + Serverless - Fargate and ECS supported, others are on roadmap + Windows - On roadmap
3. Where is AccuKnox SaaS located?
AccuKnox SaaS is deployed across multiple regions to ensure high availability, low latency, and compliance with regional data regulations. Currently, our SaaS is available in the following environments:
- United States (Primary Production Environment)
- URL: app.accuknox.com
- This is our primary production deployment serving customers across North America.
- India Production Environment
- URL: app.in.accuknox.com
- Optimized for customers in India and neighboring regions to ensure better performance and adherence to local data residency requirements.
- Europe Production Environment
- URL: app.eu.accuknox.com
- Designed to comply with GDPR and serve customers across the European Union with minimal latency.
- Middle East Production Environment
- URL: app.me.accuknox.com
- Tailored for enterprises in the Middle East, offering improved accessibility and alignment with regional compliance standards.
4. Does AccuKnox provide auto discovery of assets and workloads?
Yes, AccuKnox can auto discover assets in the cloud by leveraging the cloud native tools.
For workloads, AccuKnox agents will provide the visibility data.
5. Do I need to enable native security services for AWS to get data into Accuknox?
AccuKnox only requires an IAM role to be created with read only access to be able to get data from AWS. Security Hub and Macie can be optionally enabled for AccuKnox to gather richer telemetry data with more context.
6. What are the Hypervisors or Virtualized Environments that are supported by AccuKnox?
AccuKnox technology does not integrate at the VM virtualization layer. AccuKnox tech integrates at the operating system layer and ensures that the right hardening/enforcement for process executions, network access, and file access is in place. Thus AccuKnox can operate on any virtualization tech provided that the underlying VM uses Linux as its operating system.
7. What are the integration tools and registries that are supported by AccuKnox?
AccuKnox can integrate multiple Cloud Account, Registries, SIEM platform, Ticketing or Notifications Tools and the list is ever growing. AccuKnox is pretty flexible to support the progression of the list with the customer’s request as our roadmap item. Some of the supported today are as follows:
-
Security Events/SIEM : Splunk, Rsyslog, AWS CloudWatch, Elastic Search, Webhooks, Azure Sentinel
-
Notification Tools: Slack, Jira, PagerDuty, Emails
-
Ticketing Tools: Jira, FreshService, Connectwise, Zendesk
-
Registries: Nexus, ECR, GCR, DockerHub, ACR, Harbor
8. Can AccuKnox help in Monitoring?
-
With Accuknox, you can create monitors for assets or group of assets to get alerts for changes observed in their Metadata (software version etc)
-
Our Drift detection capability is inherently doing monitoring of the compliance checks (pass/fail) that have changed between scans.
-
We collect alerts and telemetry generated by Kubearmor and cillium. These alerts are part of our CWPP offering. These alerts are generated for the events that have violated/complied with a policy.
-
For these alerts you can have notification enabled as well through channels like Slack, email etc.
9. What will happen to my application running on a VM?
You get hardening policies via AccuKnox. AccuKnox VM Security protects virtual machines by combining CSPM, Host Scanning, Malware Scanning, CWPP, Host Hardening, and Compliance Benchmarking to prevent unauthorized access, safeguard data, and ensure compliance. It offers continuous vulnerability scanning, real-time threat detection, and remediation while minimizing the attack surface with hardened hosts and strong access controls. Overall, it provides proactive, real-time layered security and compliance assurance for virtualized environments.
CSPM (Cloud Security Posture Management)¶
1. Does AccuKnox CNAPP support only agent-based scanning or does it support agentless scanning ?
For CSPM, AccuKnox supports agentless scanning for Public Cloud Infrastructure. For Infrastructure behind a firewall or Private Cloud, AccuKnox CSPM leverages open source based agent to manage remote nodes for Automated reporting, Error log Delivery, Microservice Monitoring, User Shell Activity, Resource Monitoring.
For CWPP, AccuKnox leverages the open source CNCF sandbox project KubeArmor for scanning and in-line mitigation from known attacks. Together we provide a complete static and runtime security for a variety of workloads whether they are on Public/Private Cloud, VM, Baremetal or pure-containerized workload. Thus, we require agents to be installed to support scanning the workloads.
2. What is the differentiation of AccuKnox in Static Security?
In the Static Security solution, unlike other CSPM tools, AccuKnox provides flexibility to integrate a variety of open source and commercial security scanning tools through built-in parsers to provide you a composite security posture of your infrastructure. We also correlate and normalize results from a variety of security scanning tools and provide detailed results of vulnerabilities across infrastructure.
3. How does AccuKnox help to achieve static security?
AccuKnox Cloud Security Posture Management (CSPM) tool scans the Cloud Account to assess Vulnerabilities, Misconfigurations that are present in the cloud infrastructure based on security best practices & benchmarks. AccuKnox also enables you to handle Vulnerabilities with the ability to mark false positives, Waiting for 3rd party or Accepted risk and many more, so that you get to act on findings that are remediable and within the SLA. We also give comprehensive compliance reports based on various security governance for third party assessment operators (3PAO) auditing.
ASPM (Application Security Posture Management)¶
1. What is the differentiation of AccuKnox in ASPM Security?
In the ASPM Security solution, unlike other tools, AccuKnox provides flexibility to integrate a variety of open source and commercial security scanning tools through built-in parsers to provide you a composite security posture of your infrastructure. This is mainly done for the following two contexts:
- Remove dependencies and scoped results from one tool
- Bring in contextual understanding of vulnerabilities and prioritization based on that
Further on this, we also correlate and normalize results from a variety of security scanning tools and provide detailed results of vulnerabilities across infrastructure.
2. What components of ASPM are supported by AccuKnox?
AccuKnox provides a comprehensive ASPM solution integrated within our CNAPP. The core components include: + Static Application Security Testing (SAST) + Dynamic Application Security Testing (DAST) + Secrets Scanning + Infrastructure as Code (IaC) Scanning + Container Scanning
What are the different frameworks supported by IaC scanning?
AccuKnox's IaC scanning is designed to support industry-standard frameworks and languages. Our primary focus is on providing broad coverage for the most common tools used in modern DevOps environments, ensuring misconfigurations are identified before they reach production.
We are currently handling manual pen testing of our endpoints every few months. However, we see the risk of exposure if the DevOps/dev team makes a basic configuration change that could leave us vulnerable for a longer period. How can AccuKnox help?
AccuKnox directly addresses this gap by shifting security from periodic point-in-time assessments to a continuous, automated process. Our platform helps in the following ways: + Pipeline Integration: We integrate security checks directly into your CI/CD pipeline, catching vulnerabilities and misconfigurations automatically with every build and deployment. + Continuous Compliance: The platform continuously monitors your cloud and Kubernetes environments for configuration drift and compliance violations, providing real-time alerts. + Prioritization and Automation: Instead of manual checks, you can focus on automating security and prioritizing the most critical risks identified by the platform across your entire software development lifecycle. This "built-in, not bolted-on" approach drastically reduces the window of exposure that exists between manual penetration tests.
Does AccuKnox provide auto-patching or auto-PR creation services?
This capability is currently a work in progress and is scheduled to be available by October 2025.
Is AccuKnox tooling natively integrated with IDE?
No, AccuKnox does not provide a native IDE plugin. Our strategy focuses on integrating security at the most critical control plane: the DevOps pipeline. Users can continue using their preferred IDE and its existing tooling, while AccuKnox provides native integration with CI/CD tools like Jenkins, Azure DevOps, and GitHub Actions to ensure security is enforced centrally and consistently.
Runtime Security (CWPP & KubeArmor)¶
1. How does AccuKnox help to achieve Runtime security?
AccuKnox’s Cloud Workload Protection Platform (CWPP) achieves runtime security by leveraging CNCF sandbox project, KubeArmor, which is a cloud-native runtime security enforcement system by AccuKnox that restricts and have more granular control over the application behavior such as process execution, file access, and networking operation of containers and nodes at the system level.
2. What is the differentiation of AccuKnox in Runtime Security?
AccuKnox leverages KubeArmor, which is a cloud-native runtime security enforcement system that leverages Linux Security Modules to secure the workloads. LSMs are really powerful but they weren’t built with modern workloads including Containers and Orchestrators in mind. Hence, eBPF has provided us with the ability to extend capabilities and BPF LSM provide us with the ability to load our custom programs with decision-making into the kernel seamlessly helping us protect modern workloads. Therefore, KubeArmor helps to enforce security posture wherein any malicious attacks will be stopped before execution, known as in-line mitigation (mentioned by Forrester report)
3. What does KubeArmor leverage for enforcement and what are its advantages?
KubeArmor leverages best of breed Linux Security Modules (LSMs) such as AppArmor, BPF-LSM, and SELinux for inline mitigation to reduce the attack surface of the pod/container/VM.LSMs have several advantages over any other techniques. By using LSMs, KubeArmor does not have to disturb pods/containers and also doesn't require change at host or CRI level to apply security policies.
KubeArmor deploys as a non-privileged daemonset with certain capabilities that allows it to monitor other pods/containers and host. A given cluster can have multiple nodes utilizing different LSMs so KubeArmor abstracts away the complexities of the LSMs and provides an easy way for policy enforcement.
4. What role does AccuKnox Agents play in runtime-security?
AccuKnox Enterprise version consists of various agents such as
KubeArmor: KubeArmor is a cloud-native runtime security enforcement system that restricts the behavior (such as process execution, file access, and networking operation) of containers and nodes at the system level. KubeArmor dynamically set the restrictions on the pod. KubeArmor leverages Linux Security Modules (LSMs) to enforce policies at runtime.
Feeder Service: It collects the feeds from kubeArmor and relays to the app.
Shared Informer Agent: It collects information about the cluster like pods, nodes, namespaces etc.,
Policy Discovery Engine: It discovers the policies using the workload and cluster information that is relayed by a shared informer Agent.
5. Does KubeArmor only support Kubernetes or it can support on-prem deployments like legacy VM, pure containerized workload as well?
KubeArmor supports following types of workloads:
- K8s orchestrated workloads: Workloads deployed as k8s orchestrated containers. In this case, KubeArmor is deployed as a k8s daemonset. Note, KubeArmor supports policy enforcement on both k8s-pods (KubeArmorPolicy) as well as k8s-nodes (KubeArmorHostPolicy).
- VM/Bare-Metals workloads: Workloads deployed on Virtual Machines or Bare Metal i.e. workloads directly operating as host processes. In this case, KubeArmor is deployed in systemd mode.
6. What is the difference between Post-attack mitigation and in-line mitigation and which is better?
Post-exploit Mitigation works by killing the suspicious process in response to an alert indicating malicious intent. In this case attacker will be allowed to is able to execute its binary and could possibly disable the security controls, access logs, etc to circumvent the attack detection. By the time the malicious process is killed, it might have already deleted, encrypted, or transmitted the sensitive contents.
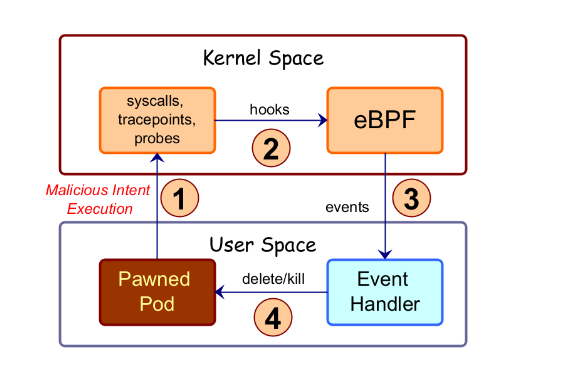
Inline Mitigation on the other hand prevents the malicious attack at the time of happening itself. It doesn’t allow the attack to happen by protecting the environment with security policy or firewall. AccuKnox’s open source tool KubeArmor provides Inline Mitigation. KubeArmor uses inline mitigation to reduce the attack surface of pod/container/VM. KubeArmor leverages best of breed Linux Security Modules (LSMs) such as AppArmor, BPF-LSM, and SELinux (only for host protection) for inline mitigation
7. Does Inline remediation slowdown the process?
LSMs are already enabled in the environment and use host based LSM security. Since the attacker usually has direct access to the pod, AccuKnox uses Inline remediation to stop the processes before executing. Therefore, inline remediation does not slow down the process
8. How to check running services in a VM?
To troubleshoot or verify if required services are running inside a Virtual Machine, use the following commands:
- To check if a specific service (e.g.,
kubearmor,vm-adapter) is running:
sudo systemctl status <service_name> # Replace with actual service name
sudo systemctl status kubearmor
sudo systemctl status vm-adapter
- To list all currently running services:
systemctl --type=service --state=running
This helps confirm whether KubeArmor or other critical services are active inside the VM for proper enforcement and telemetry.
AI Security¶
1. How does AccuKnox detect and prevent adversarial and zero-day attacks on LLMs?
AccuKnox’s AI Security applies AI-SPM with runtime behavioral monitoring, syscall tracing, and anomaly detection to identify adversarial patterns and zero-day exploits against LLM inference pipelines in real time.
2. How does AccuKnox enforce policy controls for AI workloads in Kubernetes?
Using KubeArmor integration, AccuKnox enforces fine-grained eBPF/LSM policies (process, file, and network) for AI workloads running in Kubernetes clusters, ensuring least-privilege enforcement and runtime protection.
3. How does AccuKnox secure AI data pipelines against poisoning and compliance risks?
AccuKnox provides end-to-end visibility from data ingestion to training with dataset lineage tracking, model SBOMs, and automated compliance checks (NIST AI RMF, EU AI Act, HIPAA), blocking poisoned datasets and ensuring regulatory adherence.
4. Does AccuKnox AI security cover on-premise deployed AI components?
Yes. AccuKnox provides comprehensive AI security for a wide range of deployment models. Our platform is architected to be flexible, offering robust protection for: + Public and Private Clouds + Fully On-Premise Environments + Air-Gapped Infrastructure + Hybrid Deployments This ensures your AI models, data, and infrastructure are secured, regardless of where they are deployed.
5. How does AccuKnox secure MCP servers?
AccuKnox secures Master Control Program (MCP) servers by integrating them into our Zero Trust security framework. The MCP server operates within a Sandboxed Execution environment, which provides process and network isolation. All interactions are governed by strict authorization controls and are continuously monitored, ensuring the integrity and security of the core AI orchestration layer.
6. How does AccuKnox secure AI Agents?
AccuKnox secures AI Agents through advanced runtime sandboxing and policy enforcement. Key security measures include: + Sandboxing Unsafe Tool Usage: Isolating the execution of tools invoked by agents to prevent misuse or compromise. + Sandboxing Untrusted Code: Automatically generated or untrusted code is executed in a secure, isolated sandbox (e.g., process, container, or microVM) to mitigate risks like Remote Code Execution (RCE), privilege compromise, and resource overload. This proactive approach allows organizations to leverage the power of agentic AI while defending against associated threats.
7. How does AccuKnox provide visibility into Shadow AI?
AccuKnox addresses the challenge of "Shadow AI" through its core capability of Comprehensive Visibility and Auto-Discovery. By onboarding your cloud accounts, our platform automatically discovers and inventories all AI/ML assets, including models, datasets, and compute infrastructure. This creates a single, unified view of all AI components, bringing potentially unsanctioned or unmonitored resources under the purview of the security team and allowing for the consistent application of governance and security policies.
8. How does AccuKnox help with dealing with privacy issues in AI-SPM?
AccuKnox has multiple built-in features to address data privacy: + PII/PHI Scanning of Datasets: The platform can scan AI/ML datasets to identify and flag the presence of Personally Identifiable Information (PII) or Protected Health Information (PHI). + Prompt and Response Firewalling: Our firewall inspects both the input prompts sent to LLMs and the output responses received from them to detect and block the exposure of PII/PHI in real-time.
Does AccuKnox expose privacy-related aspects to external LLMs (e.g., for AI Co-Pilot)?
No, protecting customer data is paramount. AccuKnox implements strict guardrails: + Data Sanitization: We ensure that no telemetry, alert data, or other information containing potential PII/PHI is ever sent to external LLMs for analysis or remediation suggestions. + Tenant-Level Control: The AI-assisted remediation feature can be completely disabled on a per-tenant basis, giving customers full control over whether any of their data interacts with an LLM.
Which platforms and environments does AccuKnox AI security support?
AccuKnox AI security supports a wide range of platforms and environments, including:

CDR (Cloud Detection & Response)¶
1. How does AccuKnox CDR collect security logs from cloud accounts?
AccuKnox ingests audit logs directly from cloud providers using provider-optimized methods: - AWS: Push-based via CloudTrail → S3 → ingestion. - GCP / Azure: Pull-based via Pub/Sub or Event Hub subscriptions.
2. What is required to enable automated remediation?
- GitHub Actions: Remediation scripts run from your controlled repository.
- Cloud Permissions: Admin-level access (AWS IAM admin, Azure Subscription Owner, GCP Owner) to apply fixes.
3. How does AccuKnox map detected threats to remediation actions?
Each rule violation is linked to a specific remediation script. Example: A VM with a public IP triggers a script that removes the IP automatically.
KSPM (Kubernetes Security Posture Management)¶
1. How does AccuKnox KSPM discover and monitor Kubernetes assets?
AccuKnox continuously maps clusters, namespaces, nodes, pods, and services across hybrid and multi-cloud. It provides real-time visibility, attack-path analysis, and detection of unauthorized deployments.
2. How does KSPM automate compliance checks?
AccuKnox runs continuous scans against CIS Benchmarks, NSA/CISA guidance, and MITRE ATT&CK mappings, while supporting custom policies for organization-specific governance.
3. How does KSPM integrate into CI/CD to secure workloads pre-deployment?
AccuKnox scans Kubernetes manifests, Helm charts, Terraform files, and container images for misconfigurations and CVEs before deployment, enforcing RBAC and IaC security controls.
Policy Management & Enforcement¶
1. How AccuKnox helps in Policy Version Control for Runtime Security?
Accknox enables DevSecOps teams to embed security policies as code into their GitOps workflow. This provides a unified, collaborative view of the policies and enables them to be shipped and deployed along with the applications they are protecting. Hence, utilizing Gitops based policy version control, it will be easy to enforce changes to policies and keep track of versions in case of audit or rollback requirement alongwith approval mechanisms.
2. How AccuKnox helps to achieve Microsegmentation?
AccuKnox CWPP provides micro-segmentation at the lowest possible granularity level which is also a smallest execution unit in Kubernetes i.e. Pods. We will help you to identify process execution request from the pods, network connections the pods are trying to make internally or externally and files-system the pods are accessing. By observing the behavior of a particular pod and restricting that behavior so that it functions according to the expected flow of process/events/traffic, one can develop a least permissive security posture from creating a whitelisting policies and auditing/denying everything else.
3. How AccuKnox helps to recommend Auto-Discovered Policies?
AccuKnox CWPP solution provide Discovery Engine agent that assesses the security posture of your workloads and auto-discovers the policy-set required to put the workload in least-permissive mode. We also provide Shared Informer Agent which collects information about cluster like pods, nodes, namespaces etc. The Policy Discovery Engine discovers the policies using the workload and cluster information that is relayed by Shared Informer Agent.
4. How Does AccuKnox Generate Hardening Policies?
AccuKnox operates KubeArmor to secure Kubernetes, container, and VM workloads by enforcing runtime hardening policies using Linux Security Modules (LSMs) and eBPF. The AccuKnox platform auto-discovers application behaviors and maps them to industry standards like CIS, MITRE, NIST, and STIG frameworks, generating tailored security policies to block unwanted activity at the system level. Policies can restrict process execution, file access, and network operations, helping achieve Zero Trust while maintaining compliance and visibility over what gets allowed or blocked in real time.
5. How AccuKnox helps to implement Zero Trust?
By implementing a zero trust posture with KubeArmor, organizations can increase their security posture and reduce the risk of unauthorized access or activity within their Kubernetes clusters. This can help to protect sensitive data, prevent system breaches, and maintain the integrity of the cluster. KubeArmor supports allow-based policies which result in specific actions to be allowed and denying/auditing everything else. For example, a specific pod/container might only invoke a set of binaries at runtime. As part of allow-based rules you can specify the set of processes that are allowed and everything else is either audited or denied based on the default security posture.
6. What does AccuKnox measure, while doing security posture observation and how does it help in securing using policies?
- Compliance Frameworks (MITRE, CIS, NIST) for hardening workloads are used to create hardening policies
- Understanding the Application behaviour using LSMs enables creation of behavioural policies
- Hardening policies are block based policies
- Behavioural policies are allow based policies
- An example of policies is FIM (File Integrity Monitoring) policy
7. Do you have any standard hardening rules onboarded and will the hardening policy show what is getting blocked?
Yes, it can show up in terms of Application Behaviour & Logs
Compliance & Auditing¶
1. What are all the compliance frameworks that AccuKnox is covering?
AccuKnox’s CNAPP tool checks for compliance and governance from various benchmarks like STIG, CIS, NIST CSF, HIPAA, MITRE, SOC2, ISO 27001 including AI compliances like NIST AI RMF, OWASP Top 10 LLM, EU AI Act, etc. See the full list of 33+ compliance frameworks that we support.
Deployment & Architecture¶
1. What is the deployment architecture?
AccuKnox's platform can be deployed in several flexible ways to suit different operational and security requirements:
- AccuKnox SaaS: This model offers a scalable, easy-to-use, and quick deployment experience, with upgrades and maintenance managed by AccuKnox.
- AccuKnox Managed OEM/MSSP: Designed for managed deployments where AccuKnox handles upgrades and maintenance for partners.
- AWS On-prem (Hybrid): This is a hybrid solution that combines cloud services from AWS with on-premises deployments.
- Full On-premises or Air-gapped: Provides maximum security and isolation, making it suitable for sensitive and highly regulated industries.
The on-premises deployment is based on a Kubernetes-native architecture, utilizing microservices and databases like PostgreSQL and MongoDB to manage API logic and data.
AccuKnox utilizes both agent-based and agentless approaches to provide comprehensive security across different environments:
- Agentless Security: For public cloud infrastructure security, AccuKnox operates in an agentless mode, using API scans for SaaS-based usage.
- Agent-Based Security: AccuKnox also offers robust agent-based protection for workloads:
- For Kubernetes: The platform uses a Daemonset for Kubernetes deployments.
- For Containers and VMs: AccuKnox leverages a Systemd mode for deployment on containers and virtual machines.
- On-Premises Infrastructure: For on-premises or data center deployments, the solution can be installed using Helm charts.
2. How AccuKnox helps achieve protection for Edge, 5G workloads?
AccuKnox addresses the unique security challenges of Edge and 5G environments by leveraging its core capabilities:
- Zero Trust on Kubernetes and VMs: The platform extends its Zero Trust security model to virtual machines and Kubernetes at the edge.
- Real-time Enforcement: Offers preemptive, prevention-based security for 5G control planes. The platform provides a unified view of application behavior and communication patterns in 5G networks.
- Lightweight Agent: Uses a low-footprint runtime protection agent (from the open-source project KubeArmor), leveraging eBPF and Linux Security Modules (LSM) to ensure that only necessary access and behavior rules are enforced at the OS level, even in isolated environments.
- Policy & Testing for 5G: Provides tools for creating policies for xApp/RIC, certifying security for CNF/ORAN parts, and simulating attacks for 5G networks.
3. What happens if the AccuKnox Control Plane goes down? Will runtime protection still work?
Yes. Runtime security enforcement continues even if the Control Plane is unavailable. The availability of the Control Plane does not impact the customer’s Data Plane or production operations.
4. Can AccuKnox be deployed in a distributed architecture?
Yes. AccuKnox can deploy its Control Plane across multiple regions to achieve redundancy and disaster recovery.
- Uses native Kubernetes concepts for distributed deployment.
- Nodes can span multiple Availability Zones (AZs) and regions.
- Requirement: Reliable network bandwidth between AZs/regions.
5. Can AccuKnox reuse existing infrastructure (e.g., NAT, firewalls) during on-prem deployment of the Control Plane?
AccuKnox requires an independent Kubernetes cluster for deployment. We strongly recommend not using an existing cluster running customer applications.
6. Does AccuKnox integrate with virtualization platforms such as VMware or Hyper-V?
AccuKnox does not integrate directly with virtualization platforms (VMware, Hyper-V, KVM, Nutanix AHV).
- Instead, AccuKnox secures VMs created on these platforms.
- Security is provided either agentlessly (via snapshots) or through lightweight scanning agents.
7. What is the typical timeline for a Proof of Concept (PoC)?
Typical Proof of Concept (PoC) timelines are: * SaaS PoC: ~1–2 weeks (infrastructure already in place). * On-Prem PoC: ~2–3 weeks (depends on environment complexity and readiness). * Air-gapped On-Prem: Additional time required for staging container images.
Note: In some cases where prerequisites are fully prepared, on-prem deployment has been completed in just a few hours.
8. For on-prem deployment of AccuKnox Control Plane, what are the challenges/considerations?
AccuKnox supports deployment in completely isolated environments, but some considerations apply:
-
Vulnerability Database Updates: In SaaS environments, updates are applied twice daily. In isolated deployments, customers must configure automated pipelines to push updates.
-
Container Images: Customers must stage required container images in their private registry. AccuKnox provides the image list and instructions.
-
Monitoring & Alerts: In SaaS, AccuKnox SRE practices provide automated monitoring and notifications. In isolated setups, customers need equivalent procedures.
-
Backups: Customers must configure backup/snapshot procedures, supported by AccuKnox SRE/DevOps.
9. Does AccuKnox support backup and auditing in isolated deployments?
Yes. Customers should configure backup and snapshot procedures in coordination with AccuKnox SRE/DevOps. In isolated deployments, customers are responsible for setting up monitoring and audit workflows, while AccuKnox provides guidance and support.
10. In which regions is AccuKnox deployed in?
AccuKnox is deployed in the following regions:
- US (Americas): app.accuknox.com
- Europe: app.eu.accuknox.com
- Middle East: app.me.accuknox.com
- India: app.in.accuknox.com
Pricing & Billing¶
1. What is AccuKnox’s licensing model?
You can get a custom quote and select individual security modules based on number of units (CWPP nodes, CSPM cloud assets, etc) or a comprehensive CNAPP bundle.AccuKnox offers a flexible licensing approach tailored to customer needs. It's not a one-size-fits-all model.
Customers have the flexibility to purchase specific modules such as KSPM, CSPM, ASPM, or CWPP independently. Pricing is modular and typically based on: - Number of cloud assets normalized to units - Number of container images - Number of worker nodes - Number of Tools in SCA, SAST, DAST, IaC - Number of AI/LLM Model - Bundle of per 1000 APIs Customers only pay for the modules they choose.
2. How would I know what assets are included for billing?
Count your assets here. AWS: EC2 instances, S3 buckets, RDS databases Azure: Virtual Machines, Storage Accounts, SQL Databases GCP: Compute Engine VMs, Cloud Storage buckets, Cloud SQL instances
To estimate billing, AccuKnox normalizes assets into units, refer the question above for details.
3. What happens if we exceed the asset count for a few days or weeks within a month?
The AccuKnox Control Plane will not stop you from exceeding the quota. However, if the quota consistently exceeds by more than 30% over a longer period, the AccuKnox support team will reach out for clarifications.
4. We have thousands of unused container images in our registry. Would they all be scanned?
During onboarding, you can apply filters to control which images get scanned:
- Use inclusion/exclusion regex for repo/image:tag.
- Configure to scan only images updated in the last X days or pulled within the last Y days.
- AccuKnox will notify you if the container image count exceeds 5000.
Additionally, AccuKnox supports scanning images in Kubernetes clusters or virtual machines directly, ensuring only runtime images are scanned. This reduces both the number of images scanned and findings noise.
5. How is licensing handled in SaaS and on-prem environments?
- Licensing is generally subscription-based for both SaaS and on-prem.
- On-prem customers are expected to procure Platinum Support.
6. Who to reach out to for a custom quote for CNAPP?
You can reach out to: - Sales Q's -info@accuknox.com - Technical Q's -support@accuknox.com
Partnerships & Marketplace¶
1. How do you work with partners and what are the partnership models?
We have a 100% partner aligned go to market approach. to this goal, we provide our partners the following: - Free training, certification - Joint marketing - Lead sharing For more details, please visit our partner page.
2. Current AccuKnox's marketplace listing?
AccuKnox is currently listed on:
CI/CD Integrations are also available on: - Bitbucket - Azure DevOps - GitLab - GitHub Marketplace
3. Who are AccuKnox's current partners and resellers?
We have various types of partners, including distributors and resellers, in different geographies such as the EU, US, India, and UAE. This includes System Integrators (SI), Global System Integrators (GSI), and Managed Security Service Providers (MSSP).
AccuKnox collaborates with a diverse ecosystem of partners and is available on various cloud marketplaces.
- Cloud Partnerships: AccuKnox partners with major cloud providers like AWS, Google Cloud, Microsoft Azure, Oracle Cloud, and Red Hat, offering its solutions on their respective marketplaces.
- Technology Partners: AccuKnox has alliances with companies such as Nutanix, IBM Cloud, NVIDIA, and others to ensure seamless integrations and enhanced product offerings.
- System Integrators & Distributors: AccuKnox works with System Integrators (SI), Global System Integrators (GSI), and distributors to provide customized solutions and deliver its products to customers. Examples include Wipro, NTT Data, TCS, and Carahsoft.
Resources:
4. How does the AccuKnox’s MSSP model work?
AccuKnox’s MSSP model lets managed security providers use AccuKnox’s platform to manage and secure multiple customers across different clouds, giving each client isolated access, custom policies, and easy onboarding. MSSPs can brand, automate, and scale their services—while monitoring, billing, and supporting all customers from one dashboard. Read more about our MSSP partnership program.
5. Can MSSP users access end customer tenant accounts?
Yes. AccuKnox fully supports MSSP users having viewer/editor access to end customer tenants, with customer permission. This is a critical requirement for MSSP models, and our platform is designed to accommodate it securely and seamlessly.
Roadmap¶
1. Is there a support for CIEM?
No, AccuKnox does not currently have CIEM; instead, we have KIEM. AccuKnox supports Identity and Entitlement Management for Kubernetes, referred to as KIEM (Kubernetes Identity & Entitlement Management). This capability is part of the Kubernetes Security (KSPM) module, which also handles cluster misconfiguration detection and CIS K8s benchmark findings.
2. What features are on the roadmap related to environments and integrations?
For 2025 and beyond, AccuKnox is focusing on:
CSPM Oracle Support, CSPM Azure Org Support, Assets Inventory revamp, CIEM, Custom Compliance Framework, RBAC enhancements, DSPM, Security Graph Phase I, CNAPP Policies Revamp, Collectors based ASPM onboarding, SBOM & SCA Integration, Scheduled Dashboard Reporting, AISPM: NIST AI RMF, ISO 42001, EU AI ACT, Windows / Linux Agentless VM scanning, SSPM (m365, sap), Redhat OpenShift Virtualization support, OpenStack support, Trellix (McAfee & Fireeye) Integrations, Nozomi, Armis, CTEM Integration
We will also have: - Expanded serverless support (beyond AWS Fargate/ECS). - Windows support for workloads. - Ongoing expansion of integrations with registries, SIEMs, and ticketing systems.