Integrating SAST in BitBucket CI/CD Pipeline¶
This guide explains how to integrate AccuKnox into your Bitbucket Pipelines to enhance code security using SonarQube for SAST scanning. It identifies potential vulnerabilities and sends the results to AccuKnox for further analysis and remediation.
Pre-requisites¶
-
Access to Bitbucket Pipelines
-
AccuKnox Platform Access
-
SonarQube Access
Steps for Integration¶
Step 1: Log in to AccuKnox Navigate to Settings and select Tokens to create an AccuKnox token for forwarding scan results to SaaS. For details on generating tokens, refer to How to Create Tokens.
Step 2: Add the following variables in your Bitbucket repository settings:. For details on configuring variables, refer to How to Create CI/CD Variables in Bitbucket.
-
ACCUKNOX_TOKEN: AccuKnox API token for authorization.
-
ACCUKNOX_TENANT: Your AccuKnox tenant ID.
-
ACCUKNOX_ENDPOINT: The AccuKnox API URL (e.g., cspm.demo.accuknox.com).
-
ACCUKNOX_LABEL: The label for your scan.
-
SONAR_TOKEN: Your SonarQube API token.
-
SONAR_HOST_URL: The URL of your SonarQube server.
-
SONAR_PROJECT_KEY: The project key for your SonarQube project.
Step 3: Configure Bitbucket Pipeline
| Input | Description | Default Value |
|---|---|---|
SONAR_TOKEN |
Token for authenticating with SonarQube. | N/A (Required) |
SONAR_HOST_URL |
The SonarQube host URL. | N/A (Required) |
SONAR_PROJECT_KEY |
The project key in SonarQube. | N/A (Required) |
SONAR_ORGANIZATION_ID |
Required only for SonarQube Cloud users. | "" |
SKIP_SONAR_SCAN |
Skip SonarQube scan, for advanced users. Value should be boolean. | false (boolean) |
SOFT_FAIL |
Do not return an error code if there are failed checks. | true (boolean) |
ACCUKNOX_TENANT |
The ID of the tenant associated with the CSPM panel. | N/A (Required) |
ACCUKNOX_ENDPOINT |
The URL of the CSPM panel to push the scan results to. | N/A (Required) |
ACCUKNOX_LABEL |
The label created in AccuKnox SaaS for associating scan results. | N/A (Required) |
ACCUKNOX_TOKEN |
The token for authenticating with the CSPM panel. | N/A (Required) |
Use the following YAML configuration for your bitbucket-pipelines.yml file:
definitions:
services:
docker:
memory: 3072
pipelines:
branches:
main:
- step:
name: AccuKnox SAST Scan
script:
- pipe: accu-knox/scan:2.0.0
variables:
SCAN_TYPE: SQ_SAST
SKIP_SONAR_SCAN: "false"
SONAR_TOKEN: ${SONAR_TOKEN}
SONAR_HOST_URL: ${SONAR_HOST_URL}
SONAR_PROJECT_KEY: ${SONAR_PROJECT_KEY}
ACCUKNOX_TOKEN: ${ACCUKNOX_TOKEN}
ACCUKNOX_TENANT: ${ACCUKNOX_TENANT}
ACCUKNOX_ENDPOINT: ${ACCUKNOX_ENDPOINT}
ACCUKNOX_LABEL: ${ACCUKNOX_LABEL}
Initial CI/CD Pipeline Without AccuKnox Scan¶
Initially, the CI/CD pipeline does not include the AccuKnox scan. Vulnerabilities in the code could go unnoticed without security checks.
CI/CD Pipeline After AccuKnox Integration¶
After integrating AccuKnox into the pipeline, pushing changes triggers the SonarQube scan, which sends its results to AccuKnox. AccuKnox helps identify potential code vulnerabilities.
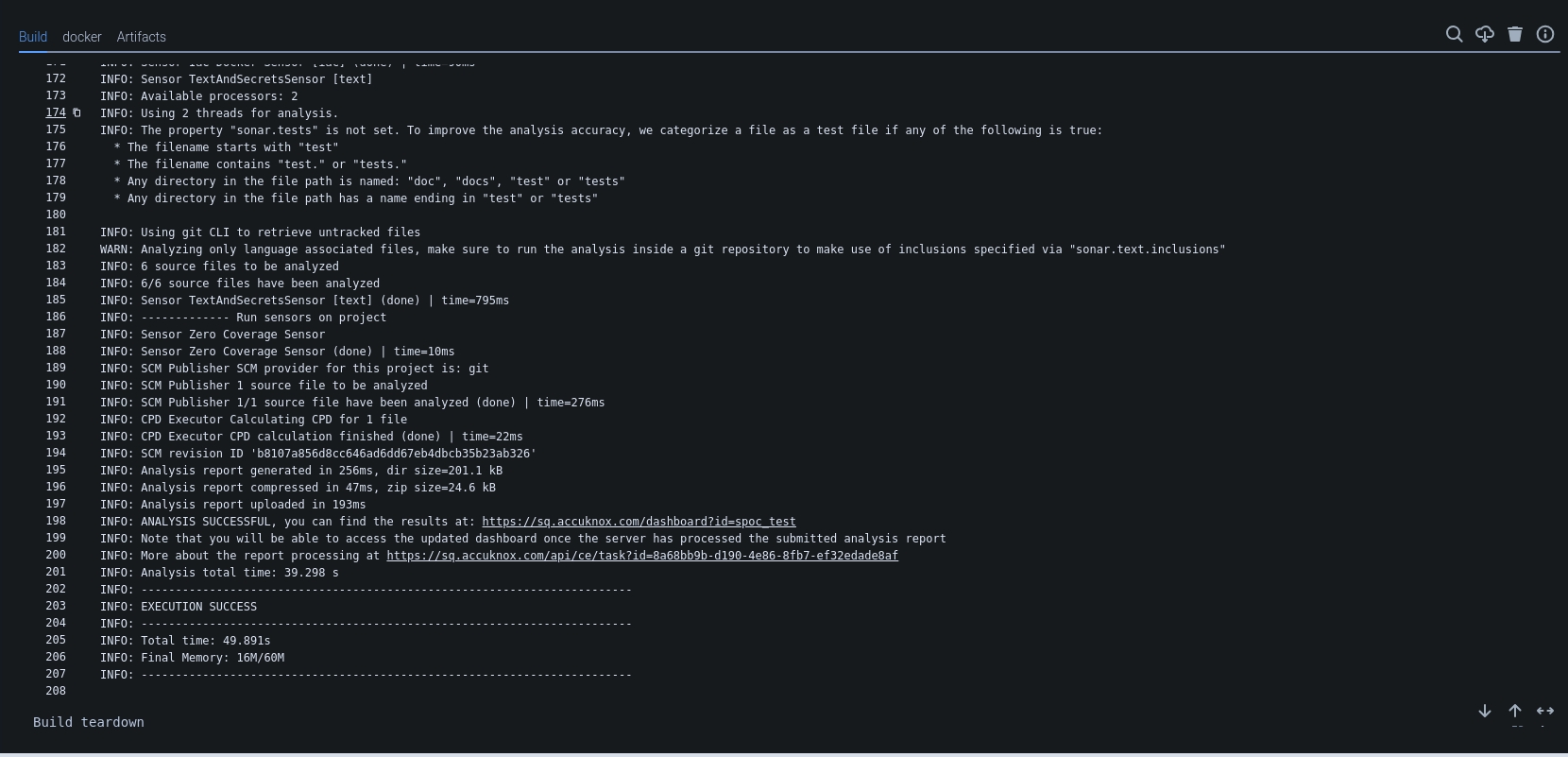
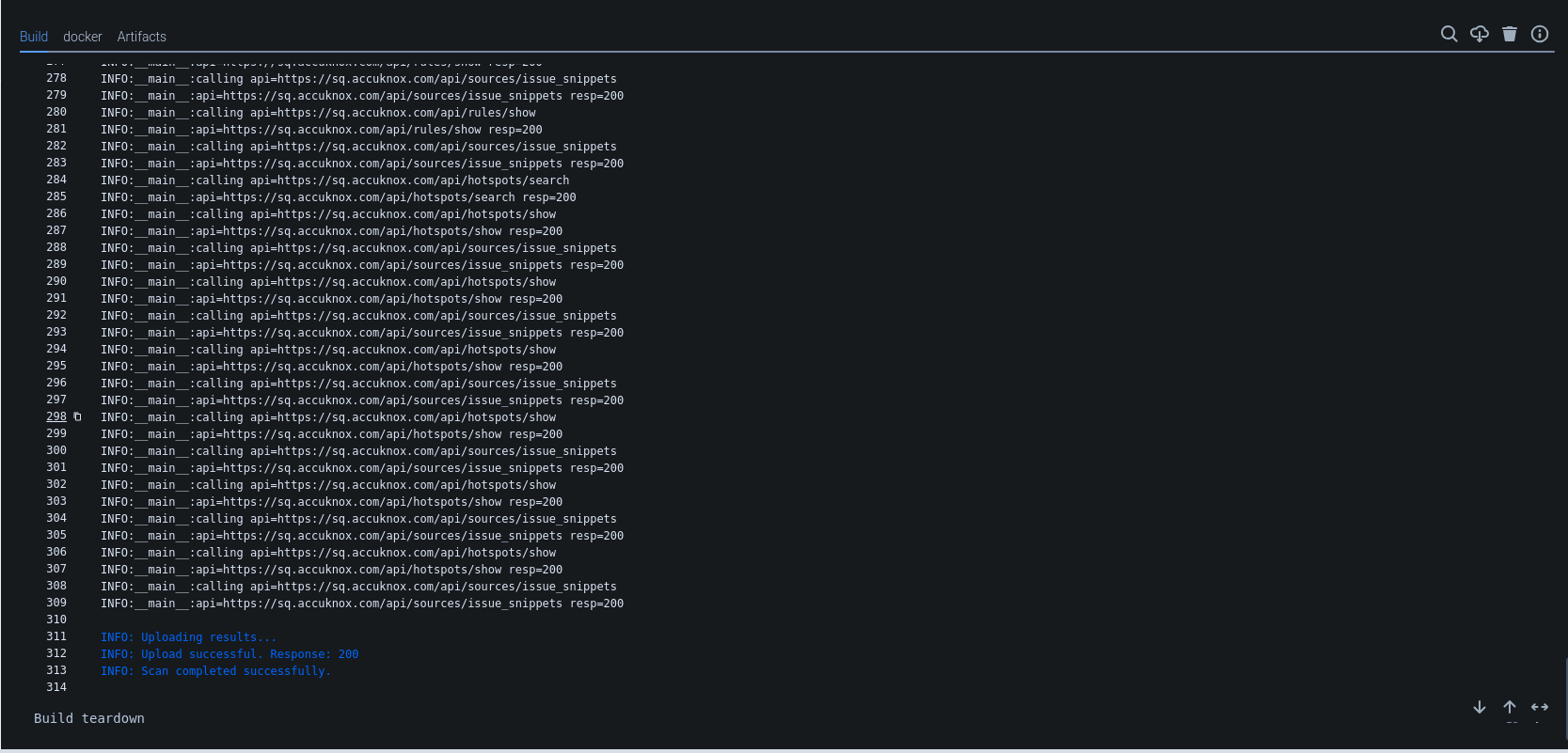
View Results in AccuKnox SaaS¶
Step 1: After the workflow completes, navigate to the AccuKnox SaaS dashboard.
Step 2: Go to Issues > Findings and select SAST Findings to see identified vulnerabilities.
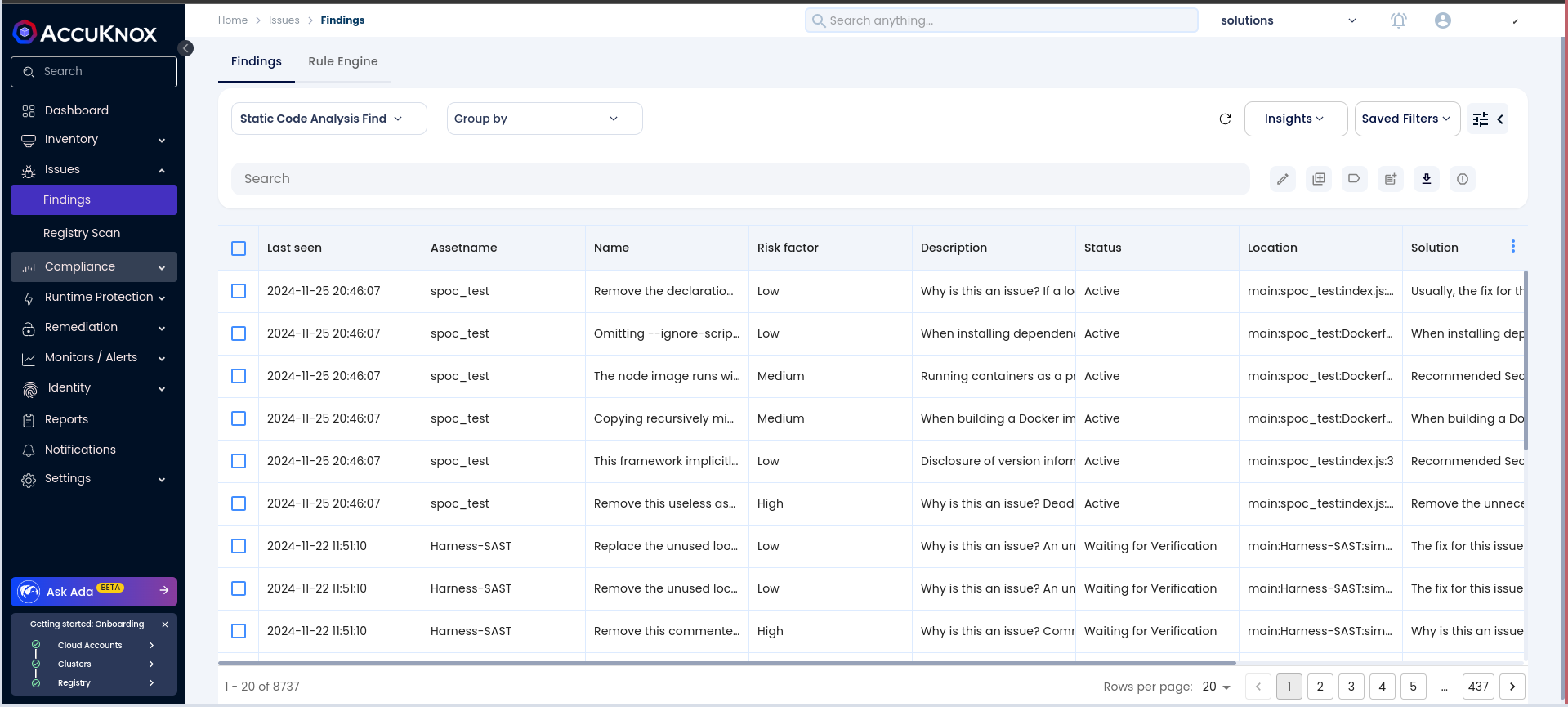
Step 3: Click on a vulnerability to view more details.
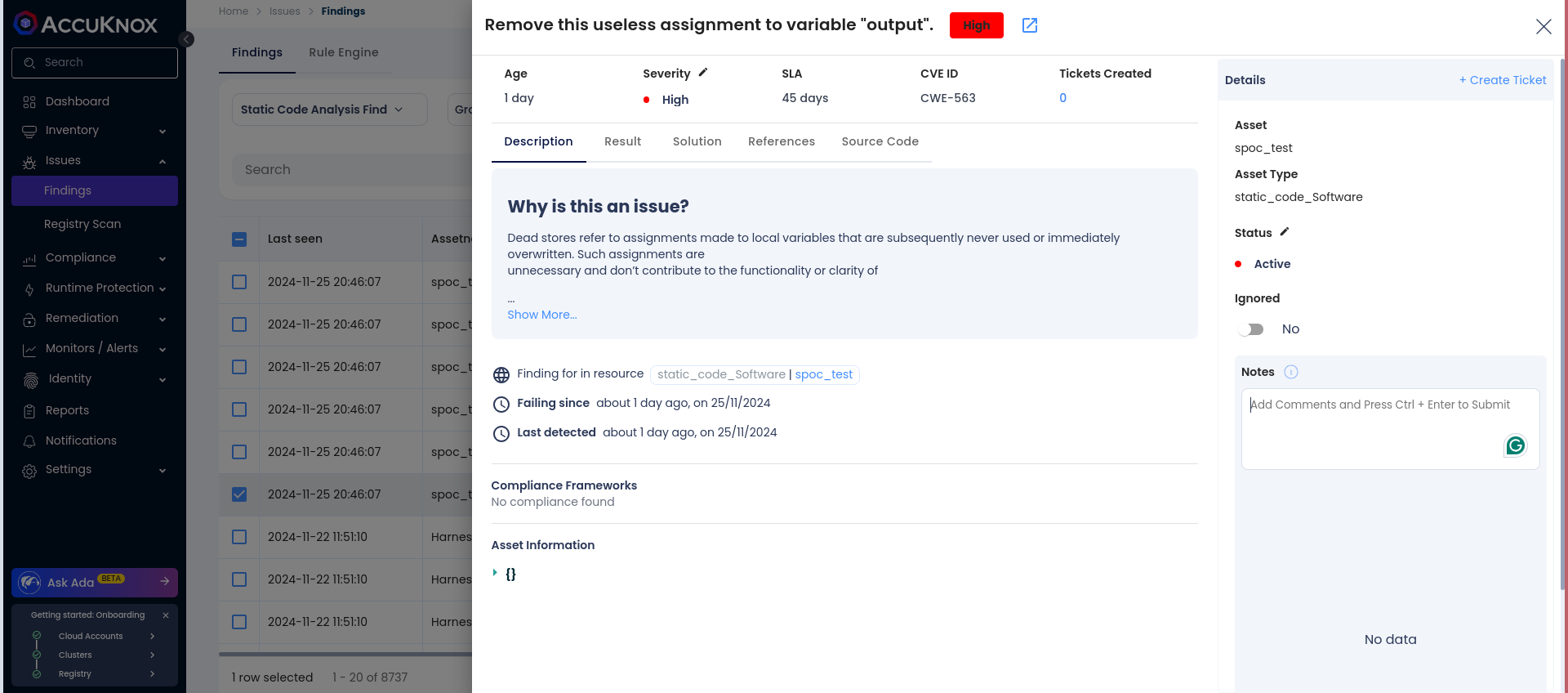
Step 4: Fix the Vulnerability
Follow the instructions in the Solutions tab to fix the vulnerability
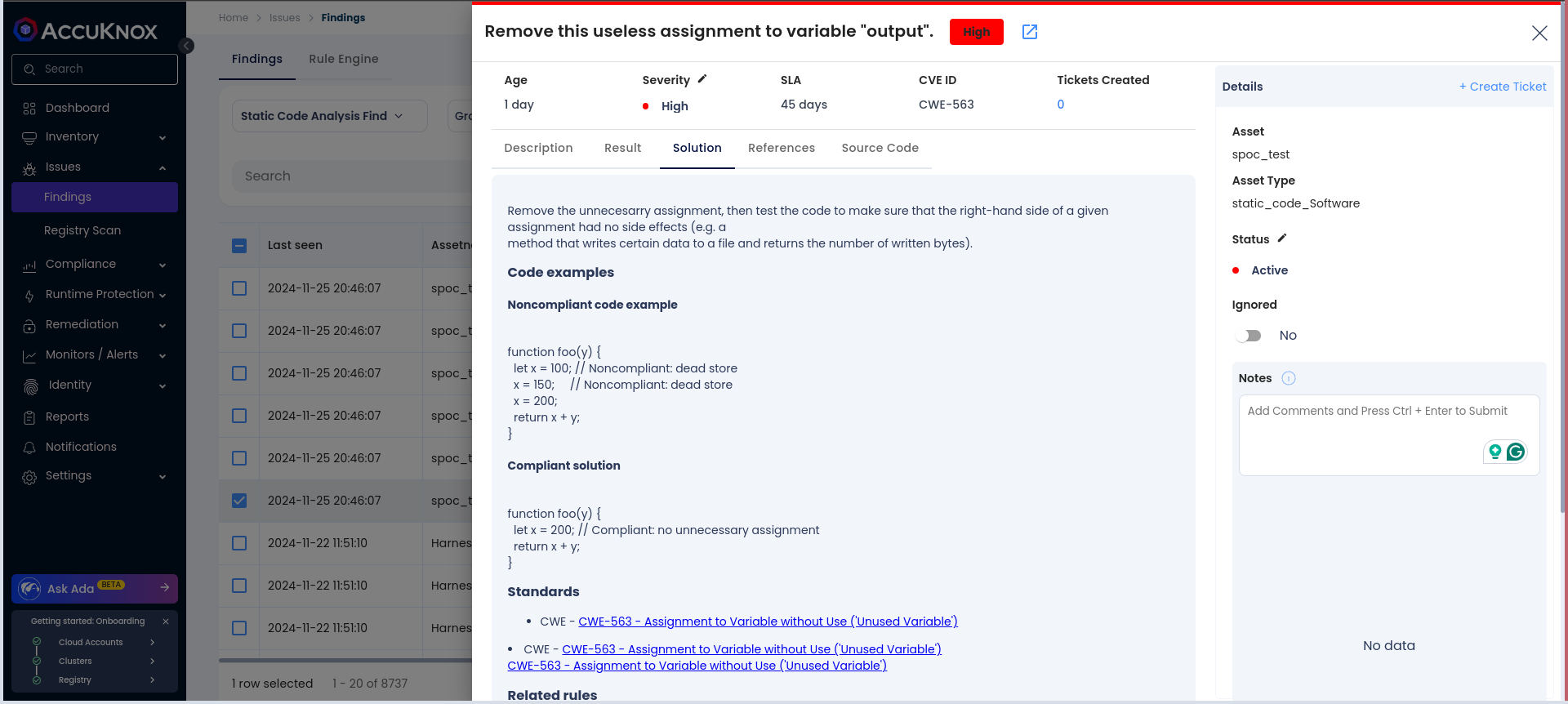
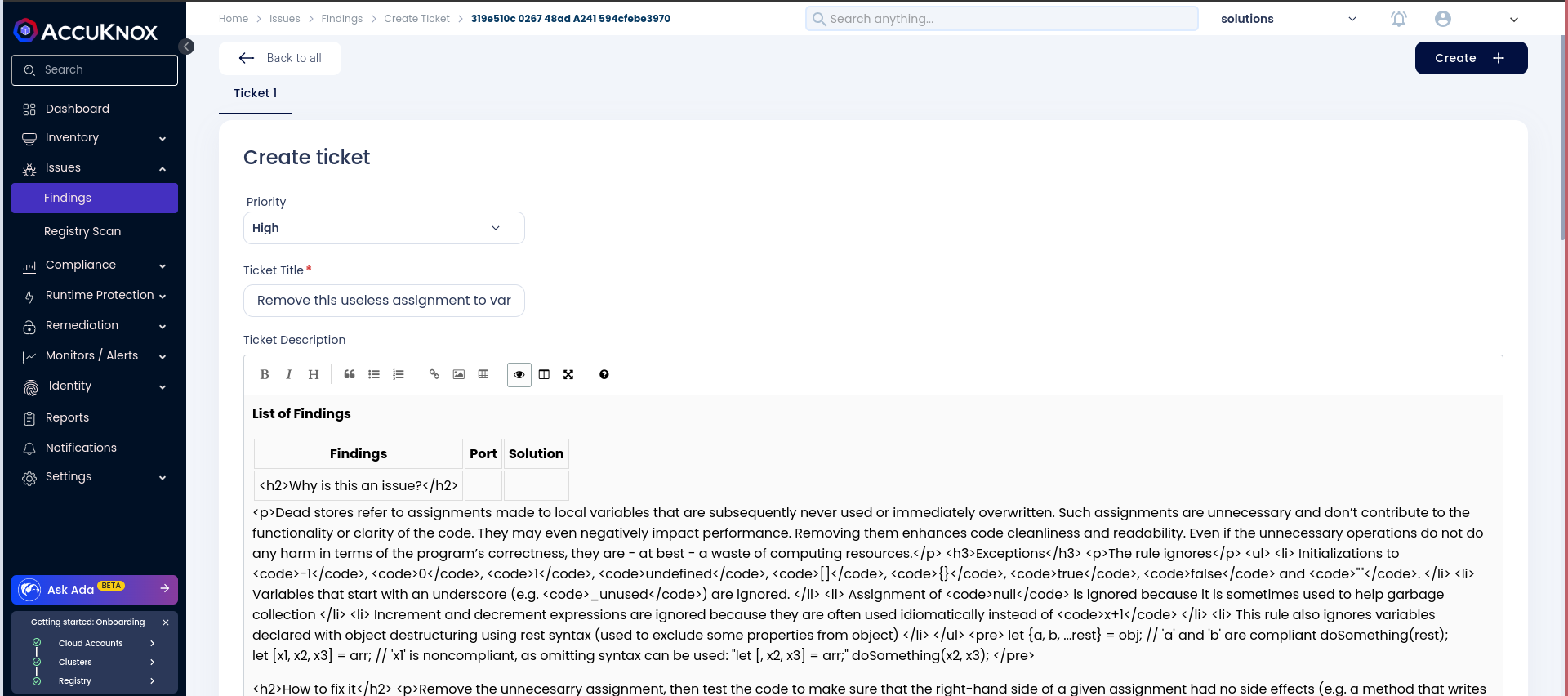
Step 5: Create a Ticket for Fixing the Vulnerability
Create a ticket in your issue-tracking system to address the identified vulnerability.
Step 6: Review Updated Results
-
After fixing the vulnerability, rerun the CI/CD pipeline.
-
Navigate to the AccuKnox SaaS dashboard and verify that the vulnerability has been resolved.
Conclusion¶
Integrating SonarQube with AccuKnox in Bitbucket Pipelines helps detect and remediate vulnerabilities early in the development lifecycle, ensuring a secure deployment environment.